Science & Technology
With the increase in the number of people coming online and storing their information on cloud - not to mention the companies harvesting tonnes more user data - the amount of data stored on the web is expected to grow monumentally.
That is expected to grow to 200 zettabytes (1 Zettabyte~100 million Terabyte) by 2025, according to Cybersecurity Ventures, an organization researching in the field of cyber security. Cybersecurity Ventures, expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015.
There are a lot of data breaches, occurring every day, and India alone accounts for 37 percent of total breaches according to Mordor Intelligence, a market research and consulting organisation.
Nepal is also facing a threat in the cyber security front. More than 50 governmental websites were reportedly hacked in 2017 and a popular service provider Vianet was breached in 2020. It is more than important to protect your data.
While having a strong password is a first step in securing your online presence, in cyberspace, with the ever-increasing risk of hacking and account compromise, there are also other ways to protect your accounts.
1. Strong Password:
Password with eight character or more in length, at least a digit, a capital letter, a symbol/character, it is not enough; albeit this is the first line of defence.
What not to put in the password (?):
- Your birthday
- Contact number
- Name or part of it
- Close relatives’ names and their contact number
You can use the passphrases, like $piderm@n in between the password to increase the complexity.
The strength of password is only good enough if you keep it secret. Don’t write your password in a paper, or in note keeping apps, neither disclose it to anyone else, at least not in email, phone or SMS.
2. Different passwords for different sites:
Passwords are like a ‘chink in someone's armour’, there is always a chance that you can get phishing attacks, or the site you are entering the credentials suffer a data breach. In that case, if the password is same for several site, your accounts on other sites are endangered as well. So, having different passwords for different sites is always an easy way to limit the blow.
It is hard to remember all your passwords, and equally easy to use a password manager to save all your passwords. But having an un-encrypted password manager is like writing your password in a note keeping apps, hackers can easily access your passkeys. Most people use browser-based password managers, but not all are encrypted.
Check if they are encrypted, encryption makes it nearly hack-proof even for the password managing companies. You can simply do a ‘Google Search’ for that.
3. 2FA:
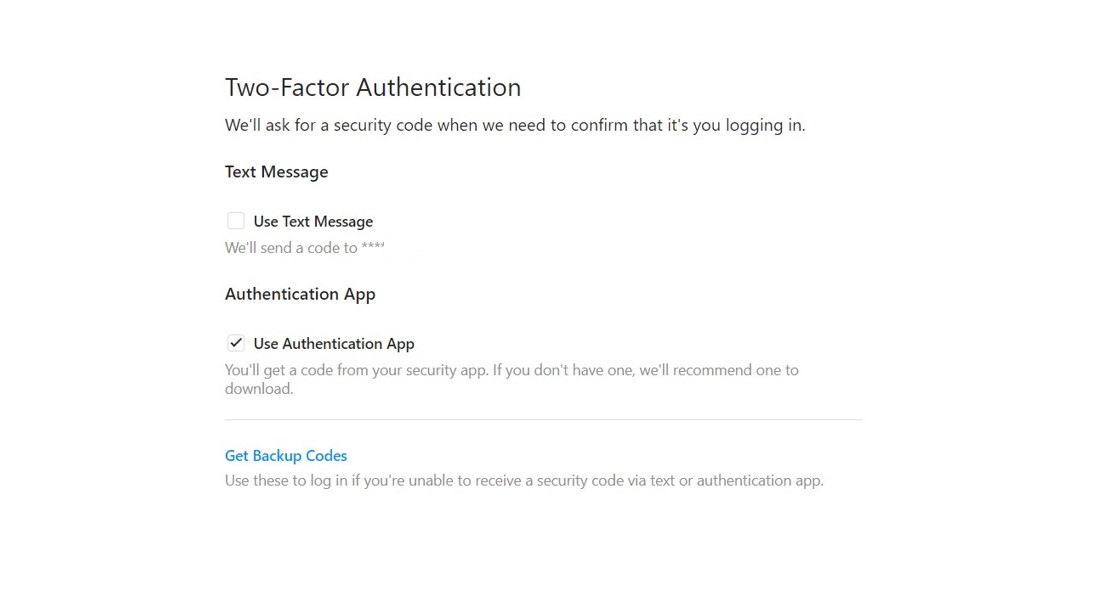
While there are still a lot of sites, which do not even have the provision of two-factor authentication (2FA); it is always wise to toggle on this feature in those sites which have.
Most of us are the social media worms and barely use other sites. There is provision of 2FA feature in most of these sites including Facebook, Twitter, Instagram, TikTok and also the email providers like Gmail and Microsoft.
What 2FA does is create a second line of defence to your supposedly strong password. There is treasure trove of stolen credentials in the dark web, and there is growing phishing attacks which can be used by black hat people. Using 2FA can protect your ID, even if they have access to your credentials by prompting to enter a code, either sent to your phone via SMS, prompt or from an authenticator app.
If the attack is sophisticated, there is a chance that criminals will be able to compromise the SMS based 2FA by sim swapping technique or snooping during transmission.
The authenticator based 2FA seems to be on the safer side, as it a device-based security and does not rely on the transferring of data over a network. The most popular authenticator apps are Google Authenticator and Microsoft Authenticator.
4. Don’t share sensitive information online
It is hard to keep things out of cyber world, when everyone is rushing after the social approval in a disguise of likes and comments. But your personal information when gets online might be used against you.
Be especially careful when you are sharing your location, which may invite a physical threat to you and your property. It is quite common to see people posting their whereabouts: Travelling to ‘places’, check-in information in hotel, restaurants, ‘places’, etc, those may put you in danger.
5. Check your privacy settings
Giving a glance to your privacy settings on your social sites, can protect you from a brewing disaster. You may not want to share some information with people or website you don’t want or trust. All social media platforms have way to limit and control the information you share. They change quite often, so it always good to have a look every now and then.
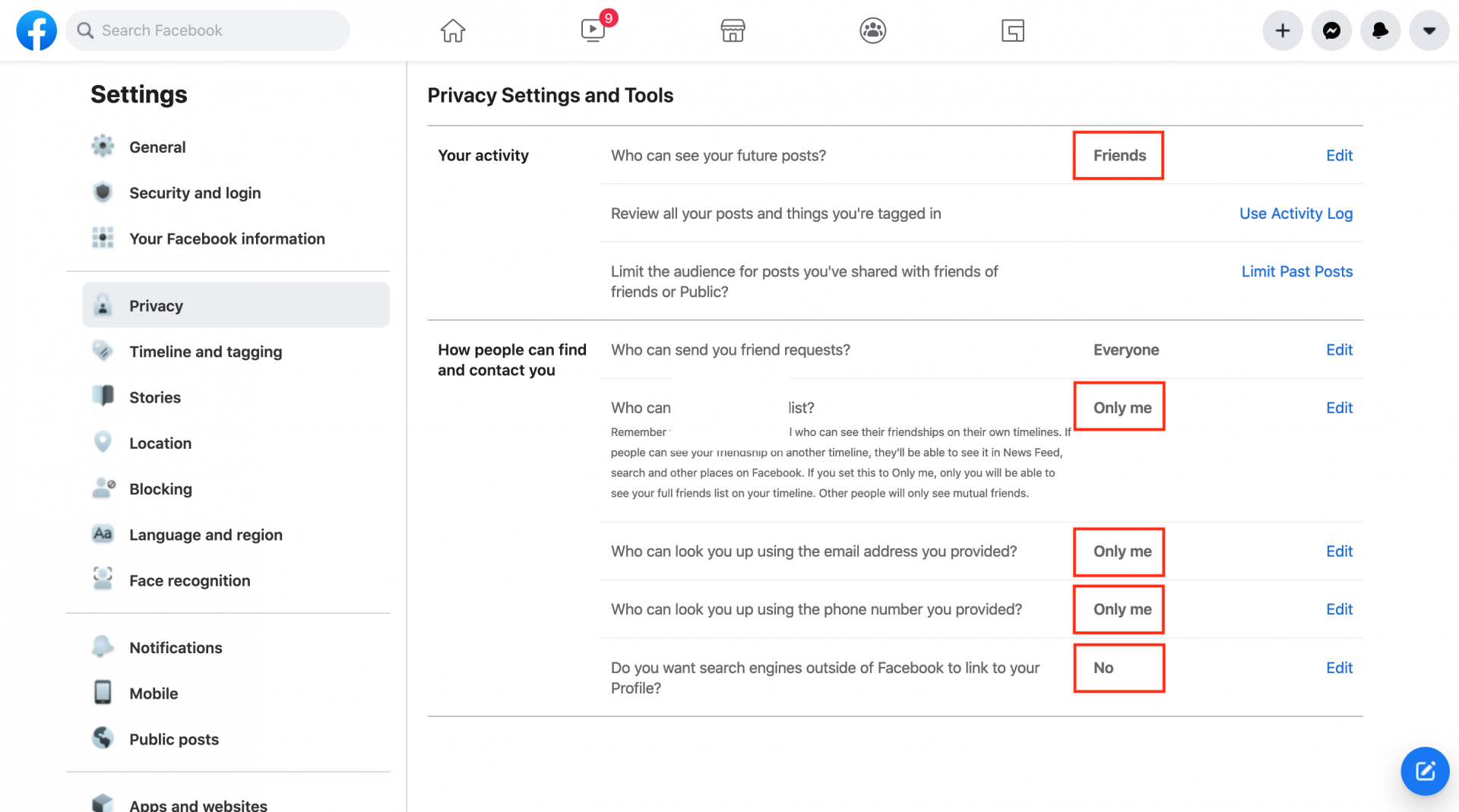
But even if you share the information with your friends and the close circle, it is only as good as your friend list. Be quite sceptical before accepting the request as you might be giving access to your social life to some strangers.
Someone in a black hat can even impersonate you to give your personal information.
One’s life is a life in a cave, if you opt out of the social media sites, there is no other way to stay connected to your family and friends. It is even harder to not participate in the social approval contest; who gets more likes?
Not just the online account protection; it is equally necessary to protect your health too, both mental and physical. It is always refreshing to have a fresh blow of air outside the room, far from gadgets.






